Bluetooth Technology for Micro-Location: A Necessary Union of Accuracy and Security
|
The many advantages of Bluetooth® Low Energy (LE) – such as low power consumption and low module cost – are not only a blessing for data transfer applications. Increasingly, they’re also embraced for tracking and positioning. Examples of such use cases include location of assets, indoor navigation, and keyless entry.
Most importantly, Bluetooth LE profits from its near-ubiquitous integration in devices such as smartphones. Naturally, this facilitates its adoption and accelerates the development of user-friendly applications.
From Bluetooth Location to Bluetooth Micro-Location
When it comes to the use of Bluetooth® LE for tracking and positioning, the best is yet to come. The reason is that we can push the accuracy of Bluetooth positioning even further than what is possible today. Key to this are novel algorithms that incorporate advanced signal processing and phase-based distance measurements. These will allow Bluetooth LE to reach precision levels in the order of centimeters.
An important characteristic of these algorithms is their ability to separate line-of-sight from multipath signals. This means Bluetooth LE maintains its accuracy in challenging environments like indoor locations where there’s a lot of reflection – such as factory halls.
Think about the explosion of new use cases that this will enable. In a warehouse, we will be able to keep track of individual packages or even envelopes. AR applications will fulfill more of their promises when it comes to merging the real and virtual world. And in-store proximity marketing will become targeted down to the level of individual products.
The Risks of Micro-Location
It’s thus clear that Bluetooth® technology can become a leading and flexible solution for an expanding range of use cases that require accurate positioning. But the success of micro-location and micro-tracking technology does not depend on accuracy alone. Security deserves at least as much attention.
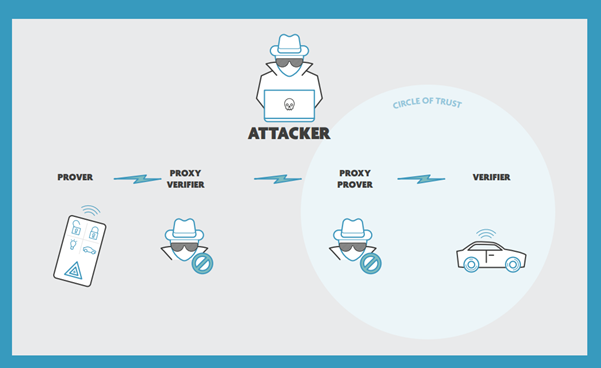
The biggest threat for the use cases outlined above is that an attacker falsifies the proximity of two legitimate entities – known as location spoofing. A well-known example of location spoofing is the relay attack. Here, a so-called relay station convinces a legitimate verifier that the legitimate prover entity is nearer than it actually is. To achieve this, an attacker uses two proxy devices: one close to the legitimate prover and one close to the legitimate verifier. It then relays the communication between these illegitimate entities.
A well-known example of such a relay attack is car theft by manipulating the passive keyless entry system of a car. Imagine a car that’s parked in front of a house. You would assume that the car key, inside the house, is far enough from the car to ensure that the lock is safe. But, by using relay boxes, thieves can capture wireless signals through walls, windows, doors, etc. and relay these from car to key and vice versa.
Airtight Security
The good news is that Bluetooth® LE is a technology that can offer airtight security against this type of risk. However, it’s important to realize that a threat such as a relay attack cannot be prevented by uniquely using cryptographic procedures. Why not? Because such an attack requires no knowledge of the data that’s transmitted.
What’s needed is careful codesign of wireless technology hardware and cryptographic features. This will enable Bluetooth LE to become a standard for accuracy and security in the domain of location and tracking.
Want to find out more? Register to attend our webinar for more exciting use cases of Bluetooth micro-location and the technological advances that will enable it.